Shortcuts
Title Page
A Novel Anti-Phishing Framework Based on HoneypotsShujun Li1 and Roland Schmitz2
1 University of Konstanz, Germany
2 Stuttgart Media University, Germany
In Proceedings of 4th Annual APWG eCrime Researchers Summit 2009 (APWG eCrime/eCRS 2009, Tacoma, WA, USA, October 20 & 21, 2009), IEEE.
Copyright 2009 IEEE. Published in Proceedings of 4th Annual APWG eCrime Researchers Summit 2009 (APWG eCrime/eCRS 2009, Tacoma, WA, USA, October 20 & 21, 2009), 2009, DOI: 10.1109/ECRIME.2009.5342609. Personal use of this material is permitted. However, permission to reprint/republish this material for advertising or promotional purposes or for creating new collective works for resale or redistribution to servers or lists, or to reuse any copyrighted component of this work in other works, must be obtained from the IEEE. Contact: Manager, Copyrights and Permissions / IEEE Service Center / 445 Hoes Lane / P.O. Box 1331 / Piscataway, NJ 08855-1331, USA. Telephone: + Intl. 908-562-3966.
Abstract
As a powerful anti-phishing tool, honeypots have been widely used by security service providers and financial institutes to collect phishing mails, so that new phishing sites can be earlier detected and quickly shut down. Another popular use of honeypots is to collect useful information about phishers’ activities, which is used to make various kinds of statistics for the purposes of research and forensics. Recently, it has also been proposed to actively feed phishers with honeytokens. In the present paper, we discuss some problems of existing antiphishing solutions based on honeypots. We propose to overcome these problems by transforming the real e-banking system itself into a honeypot equipped with honeytokens and supported by some other kinds of honeypots. A phishing detector is used to automatically detect suspicious phishers’ attempts of stealing money from victims’ accounts, and then ask for the potential victims’ reconfirmation. This leads to a novel anti-phishing framework based on honeypots. As an indispensable part of the framework, we also propose to use phoneybots, i.e., active honeypots running in virtual machines and mimicking real users’ behavior to access the real ebanking system automatically, in order to submit honeytokens to pharmers and phishing malware. The involvement of phoneybots is crucial to fight gainst advanced phishing attacks such as pharming and malware-based phishing attacks.Links
- The paper: http://www.hooklee.com/Papers/APWG-eCRS2009.pdf (5.07 MB)
- The Poster: Papers/APWG-eCRS2009-Slides.pdf (1.61 MB)
- BibTEX: Papers/APWG-eCRS2009.txt
Phishing Information Flow vs. Anti-Phishing Measures
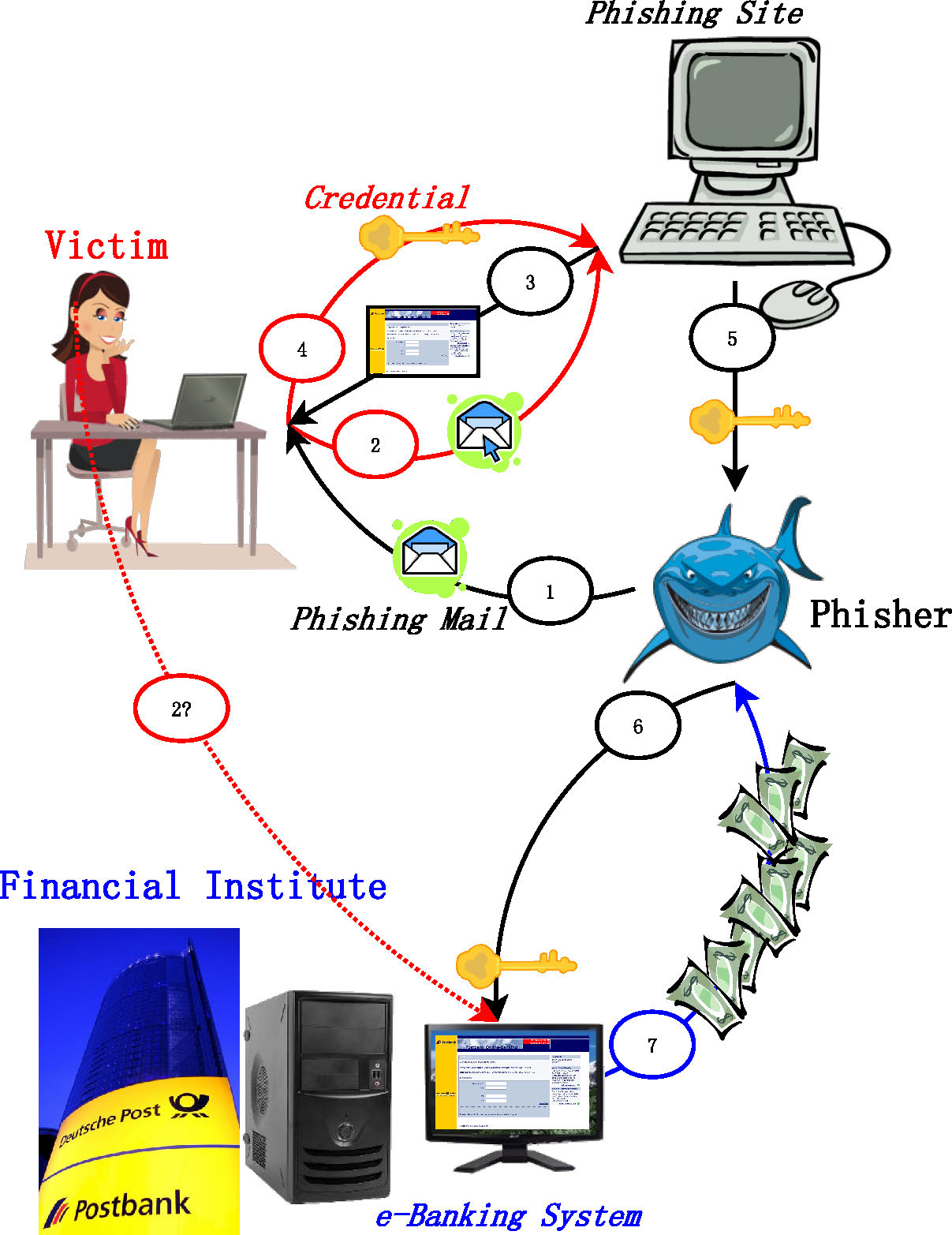 |
|
Existing Anti-Phishing Honeypots: Problems and Solutions
Why Honeypots?
- It is theoretically possible to reach 100% (or nearly 100%) detection rate because no legitimate users will try to visit honeypots.
- Honeypots are also independent of end users, since they interact only with attackers.
Existing Anti-Phishing Honeypots
- Spamtraps (honeypots against spammers) have been widely used to detect phishing emails [1, Section 5.4 and Chapter 11].
- Honeytokens or Phoneytokens ("phishing honeytokens") [2,3] have been proposed by other researchers, which are honeypots in the forms of electronic information (e.g., digital entities).
- Phoneypot ("phishing honeypot") [4], a fake e-banking services, have also been proposed to trace how how phishers use phoneytokens, which are submitted by financial institutes to already known phishing sites.
- Commercial products/services exist: RSA® FraudActionSM, MarkMonitor's Dilution™ and Phish Tagging.
Problems & Solutions
-
Problem 1: There is a gap between spamtraps and phoneytokens.
- Solution: Spamtraps+Phoneytokens or even better Spamtraps+Human manager+Phoneytokens
-
Problem 2: Phoneytokens can be verified easily if they cannot be used to access the e-banking server.
- Solution: Honeying the real e-banking system: phoneytokens can be used for login exactly like real credentials, phoneytokens + phoneypot = a simulated e-banking system.
-
Problem 3: There is a gap between the phoneypot and the real ebanking system.
- Solution: The e-banking system should be deep honeyed: real fund transfer should be supported to some extent. => The main goal is to prolong the lifespan of phoneytokens.
-
Problem 4: Spamtraps cannot defeat advanced phishers (those based on pharming or malware).
- Solution: Phoneybot = honeypot as a robot against phishing.
-
Problem 5: Outsourcing security is problematic.
- Solution: Security should NOT be outsourced: the whole anti-phishing chain should be under the control of the financial institute, but cooperation between different financial institutes and anti-phishing bodies is still very important.
Our Anti-Phishing Framework
- A complete anti-phishing chain established
-
Four different kinds of honeypots in one system
- A honeyed e-banking system as a phoneypot
- A number of phoneytokens as fake credentials supported by the honeyed e-banking system
- A number of spamtraps for attracting phishing emails and submitting phoneytokens to phishing sites
- A number of phoneybots for submitting phoneytokens to pharmers and phishing malware
- User reconfirmation via out-of-band (OOB) channel
-
Phishing detector vs. Phishers
- No alert if a fund transfer is below a threshold H
- Attacker’s behavior is considered
- A probabilistic analysis is included
- No requirement/dependence for/on the user
- Devil is in the detail: so read our paper to find out more!

Appendix: Two Enhanced TAN Schemes
In the appendix of this paper, we also proposed two enhanced TAN schemes that can resist phishing attacks more effectively than the still widely-used iTAN scheme in German banking sector.Advanced iTAN
- Index all TANs by random strings rather than ordered integers.
- The phisher is forced to guess the random string, which can be detected by the user with high probability.
Double-TAN
- For online transactions, ask for two TANs.
- For all other operations (login, changing password, etc.), ask for one or no TAN.
References
[1] M. Jakobsson and S. Myers, Eds., Phishing and Countermeasures: Understanding the Increasing Problem of Electronic Identity Theft, John Wiley & Sons, Inc., 2007.[2] M. Chandrasekaran, R. Chinchani and S. Upadhyaya, "PHONEY: Mimicking user response to detect phishing attacks," in Proc. WoWMoM 2006, pp. 668-672, IEEE Computer Society, 2006.
[3] C. M. McRae and R. B. Vaughn, "Phighting the phisher: Using web bugs and honeytokens to investigate the source of phishing attacks," in Proc. HICSS 2007, Article 270c, IEEE Computer Society, 2007.
[4] D. Birk, S. Gajek, F. Grobert and A.-R. Sadeghi, "Phishing phishers—observing and tracing organized cybercrime," in Proc. ICIMP 2007, IEEE Computer Society, 2007.