Shortcuts
What are graphical passwords?
- Graphical Passwords = Visual Passwords
-
Three main classes
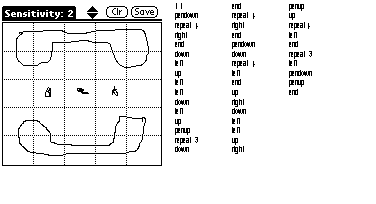
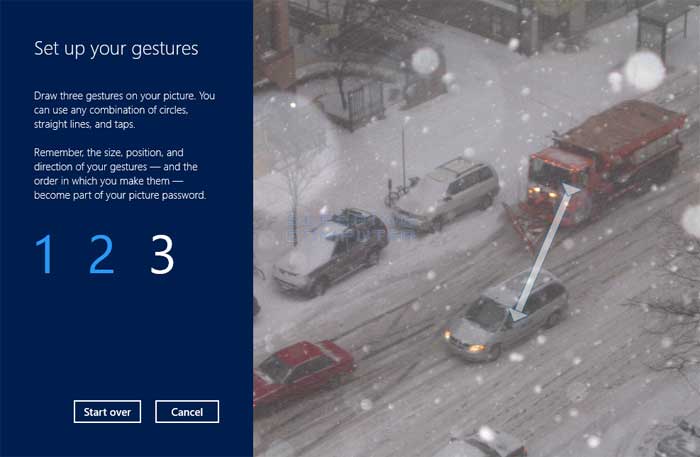
- Recall-Based Systems: drawing your passwords
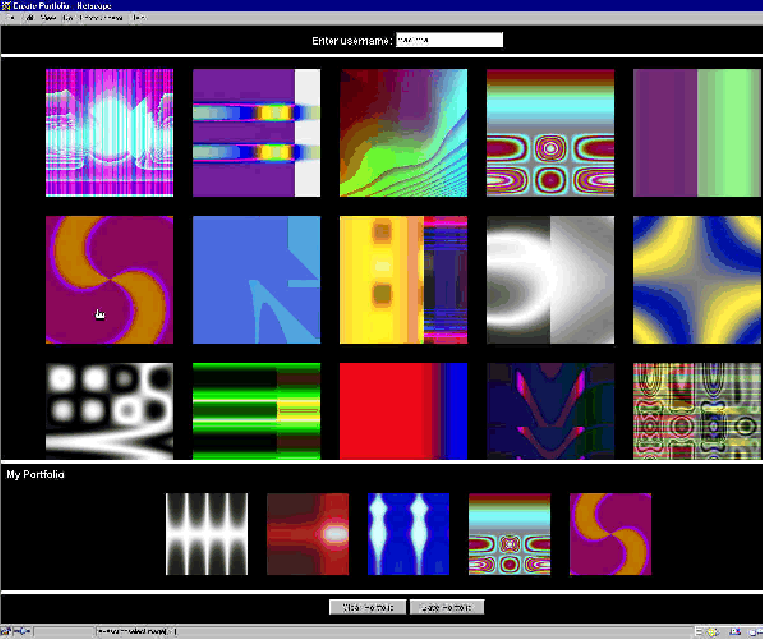
- Recognition-Based Systems: remember your pass-pictures
- Cued-Recall Systems: remember your pass-points (in a picture)
-
Two surveys you can read to learn more:
- Robert Biddle, Sonia Chiasson and P. C. van Oorschot, "Graphical Passwords: Learning from the First Twelve Years," ACM Computing Surveys, vol. 44, no. 4, Article No. 19, ACM, August 2012
- Xiaoyuan Suo, Ying Zhu and G. Scott Owen, "Graphical Passwords: A Survey," in Proceedings of the 21st Annual Computer Security Applications Conference (ACSAC 2005), IEEE Computer Society, 2005
Why do we need graphical passwords?
|
 |
Selected graphical password schemes
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
More Graphical Password Schemes: KeyWalker
Are graphical passwords really so good?
Unfortunately, the answer is no.-
Users' choices of pass-pictures in recognition-based systems are not random!
- Darren Davis, Fabian Monrose and Michael K. Reiter, "On User Choice in Graphical Password Schemes," in Proceedings of 13th USENIX Security Symposium, pp. 151-164, USENIX Association, 2004
-
Users' drawings in recall-based systems are not random, either!
- Adam J. Aviv, Devon Budzitowski and Ravi Kuber, "Is Bigger Better? Comparing User-Generated Passwords on 3x3 vs. 4x4 Grid Sizes for Android’s Pattern Unlock," in Proceedings of the 31st Annual Computer Security Applications Conference (ACSAC 2015), pp. 301-310, ACM, 2015
- Sebastian Uellenbeck, Markus Dürmuth, Christopher Wolf and Thorsten Holz, "Quantifying the Security of Graphical Passwords: The Case of Android Unlock Patterns," in Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security (CCS 2013), pp. 161-172, ACM, 2013
-
There are hotspots in cued-recall systems! => Dictionary attacks still work!
- Paul C. van Oorschot, Amirali Salehi-Abari and Julie Thorpe, "Purely Automated Attacks on PassPoints-Style Graphical Passwords," IEEE Transactions on Information Forensics and Security, vol. 5, no. 3, pp. 393-405, 2010
- Julie Thorpe and P.C. van Oorschot, "Human-Seeded Attacks and Exploiting Hot-Spots in Graphical Passwords," in Proceedings of 16th USENIX Security Symposium, pp. 103-118, USENIX Association, 2007
- Amirali Salehi-Abari, Julie Thorpe and P.C. van Oorschot, "On Purely Automated Attacks and Click-Based Graphical Passwords," in Proceedings of 24th Annual Computer Security Applications Conference (ACSAC 2008), IEEE Computer Society, 2008
-
Dictionary attacks still work on recall-based systems as well!
- Ziming Zhao, Gail-Joon Ahn, Jeong-Jin Seo and Hongxin Hu, "On the Security of Picture Gesture Authentication," in Proceedings of the 22nd USENIX Security Symposium, pp. 383-398, USENIX Association, 2013
- Amir Sadovnik and Tsuhan Chen, "A Visual Dictionary Attack on Picture Passwords," in Proceedings of 2013 IEEE International Conference on Image Processing (ICIP 2013), pp. 4447-4451, IEEE, 2013
- Julie Thorpe and Paul C. van Oorschot, "Graphical Dictionaries and the Memorable Space of Graphical Passwords," in Proceedings of 13th USENIX Security Symposium, pp. 135-150, USENIX Association, 2004
-
"The cognitive aspects of visual information processing would appear to make the use of spatial position untenablefor authentication systems."
- Karen Renaud and Antonella De Angeli, "My password is here! An investigation into visuo-spatial authentication mechanisms," Interacting with Computers, vol. 16, no. 6, pp. 1017-1041, Elsevier, 2004
What has Shujun Li been doing on graphical passwords?
-
Cryptanalysis of graphical password systems against passive observers
- Hassan Jameel Asghar, Ron Steinfeld, Shujun Li, Mohamed Ali Kaafar and Josef Pieprzyk, "On the Linearization of Human Identification Protocols: Attacks based on Linear Algebra, Coding Theory and Lattices," IEEE Transactions on Information Forensics and Security, vol. 10, no. 8, pp. 1643-1655, IEEE, 2015
-
Hassan Jameel Asghar, Shujun Li, Ron Steinfeld and Josef Pieprzyk, "Does Counting Still Count? Revisiting the Security of Counting based User Authentication Protocols against Statistical Attacks," in Proceedings of 20th Annual Network & Distributed System Security Symposium (NDSS 2013), Internet Society, 2013 (Acceptance rate: 47/250=18.8%)


 [Full Edition: IACR ePrint 2012/659]
[Full Edition: IACR ePrint 2012/659]
-
Hassan Jammel Asghar, Shujun Li, Josef Pieprzyk and Huaxiong Wang, "Cryptanalysis of the Convex Hull Click Human Identification Protocol," International Journal of Information Security, vol. 12, no. 2, pp. 83-96, Springer, 2013


-
Toni Perković, Asma Mumtaz, Yousra Javed, Shujun Li, Syed Ali Khayam and Mario Čagalj, "Breaking Undercover: Exploiting Design Flaws and Nonuniform Human Behavior," in Proceedings of 7th Symposium On Usable Privacy and Security (SOUPS 2011, Carnegie Mellon University in Pittsburgh, PA, USA, July 20-22, 2011), ACM, 2011 (Acceptance rate: 15/45=33.3%)

 © Authors
© Authors
-
Hassan Jammel Asghar, Shujun Li, Josef Pieprzyk and Huaxiong Wang, "Cryptanalysis of the Convex Hull Click Human Identification Protocol," in: Information Security: 13th International Conference, ISC 2010, Boca Raton, FL, USA, October 25-28, 2010, Revised Selected Papers, Lecture Notes in Computer Science, vol. 6531, pp. 24-30, 2011 (Acceptance rate: 37/134=27.6%)


 [Full Edition: IACR ePrint 2010/478] © Springer-Verlag GmbH
[Full Edition: IACR ePrint 2010/478] © Springer-Verlag GmbH
-
Shujun Li, Hassan Jameel Asghar, Josef Pieprzyk, Ahmad-Reza Sadeghi, Roland Schmitz and Huaxiong Wang, "On the Security of PAS (Predicate-based Authentication Service)," in Proceedings of 25th Annual Computer Security Applications Conference (ACSAC 2009, Honolulu, Hawaii, USA, December 7-11, 2009), pp. 209-218, 2009, DOI: 10.1109/ACSAC.2009.27 (Acceptance rate: 44/224=19.6%)


 [IACR ePrint 2009/476]
[IACR ePrint 2009/476] 
 © IEEE
© IEEE
-
New designs of secure human-computer interface (SecHCI) against observation attacks and graphical implementations
-
Hassan Jameel Asghar, Shujun Li, Ron Steinfeld and Josef Pieprzyk, "Does Counting Still Count? Revisiting the Security of Counting based User Authentication Protocols against Statistical Attacks," in Proceedings of 20th Annual Network & Distributed System Security Symposium (NDSS 2013), Internet Society, 2013 (Acceptance rate: 47/250=18.8%)


 [Full Edition: IACR ePrint 2012/659]
[Full Edition: IACR ePrint 2012/659]
-
Shujun Li and Heung-Yeung Shum, "Secure Human-Computer Identification against Peeping Attacks (SecHCI): A Survey," technical report, Jan. 2003 (an early version has been published online in Elesevier Science's Comuter Science Preprint Archive, vol. 2003, no. 1, pp. 5-57, 2003)

-
Shujun Li and Heung-Yeung Shum, "Secure Human-Computer Identification (Interface) Systems against Peeping Attacks: SecHCI," IACR's Cryptology ePrint Archive: Report 2005/268, received on 12 Aug 2005 (an early version has been appeared online in Elesevier Science's Comuter Science Preprint Archive, vol. 2004, no. 3, pp. 21-69, 2004)

-
Hassan Jameel Asghar, Shujun Li, Ron Steinfeld and Josef Pieprzyk, "Does Counting Still Count? Revisiting the Security of Counting based User Authentication Protocols against Statistical Attacks," in Proceedings of 20th Annual Network & Distributed System Security Symposium (NDSS 2013), Internet Society, 2013 (Acceptance rate: 47/250=18.8%)
- Design of new graphical passwords based on fractals and other interesting stuff (ongoing research)
- Combine graphical passwords with other computer security applications (ongoing research)
- Password checker for graphical passwords